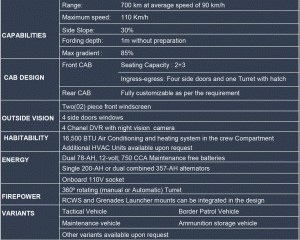
RF Jammer Apps
Opinion about the RF Jammer Apps An RF Jammer Apps is used to controlled or blocked signals from mobile devices, in order to protect private spaces. It helps to controlled noise omitted by these devices in places such as cinema, meetings and others. Although the app has been used and is accepted by most, some sees this as an infringement of their rights. The legality of using an RF Signal Jammer is up for debate, nevertheless it is commonly used.…